Fraud Alert: "Live-Chatting" for Dollars
New fraud plays on false online trust
- |
- Written by Chris Silveira

| Banks use live-chat features to help out customers. But more verification will help prevent online chat from becoming an invite to crime. | ||
Amidst the whirlwind of highly sophisticated and technology-driven Distributed Denial of Service (DDoS) attacks on financial institutions, a quieter, less hyped danger lurks--human fraudsters executing more manual, but very clever tactics to commit fraud using a combination of techniques. "Human fraud" remains alive, well, and creative--and poses great risk to financial institutions.
Guardian Analytics Fraud Intelligence team has uncovered a new twist in use: Criminals use online banking in fresh way to commit fraud--once they have successfully taken over an online account, they leverage the online chat feature as a means to manipulate customer service agents into executing wire payments.
This is a novel twist combining online banking and call center fraud. It is a powerful reminder that there are multiple ways criminals get into online accounts and multiple ways they move money out. Financial institutions need strategies that give them complete visibility into what is happening in an account and protects them from the widest array of attacks.
How "chatting for dollars" works
Here is how the scheme works. Note that along the way, there are clues that something is amiss in the account itself.
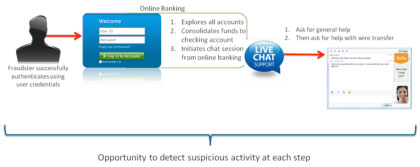
1. The game begins. The criminal logs into online banking using stolen credentials. He does so from a computer and an internet service provider that typically used by the legitimate user.
2. Digging around. The fraudster does some initial account reconnaissance and fraud setup. This includes such tasks as checking the victim's account balances and completing internal transfers into the checking account, sometimes from multiple accounts. But no transaction is initiated via online payment.
3. The chat begins. The fraudster enters into one or more live chat sessions (an instant message style chat, not over the phone) with a customer service agent.
4. The nonchalant fraud. The fraudster requests assistance with a few benign items and then ultimately enlists the customer service agent to help them with a wire transfer. The helpful customer service agent dutifully assists in processing the wire, typically for amounts $8,000 or under.
Why does this get so far?
Presumably because the fraudster had already authenticated himself through the online banking procedures, there is a high level of trust that the customer service agent places in the "user" on the other end of the chat.
Further, because the criminal is in online banking, there's access to information that can be used to further "verify" their identity. And, with the use of an instant message style chat, there would be no verbal cues or pauses to cause a savvy customer service agent to pause. And, as you can imagine, particularly with the Denial of Service attacks disrupting service, agents are likely to be over-vigilant about being helpful.
Proactively identifying suspicious behavior
This scenario supports the critical need for financial institutions to proactively identify suspicious activities leading up to a transaction. There were traces left along the way that something was amiss in the account,
The behavior exhibited by the fraudster was different than that typically exhibited by each individual legitimate user. For example:
- The login computer and location were unusual for the victim.
- The transfer of money between accounts was not an uncommon occurrence, but the amounts were much larger than the user's typical transfer.
- The use of the chat feature itself was unusual for this customer.
- And the use of wire and the amounts were all unusual.
Banks must monitor all online account behavior, not merely transactions, to detect suspicious or anomalous activities.
Detecting anomalous behavior in accounts is not only a proven approach to proactively detecting account takeover and fraudulent transactions, but is also a minimum requirement for layered security cited in the 2011 Supplement to Authentication in an Internet Banking environment (see page five). The escalation in the DDoS attacks and the continued innovation in fraud techniques are expected to increase the attention paid to these minimum requirements in 2013 examinations.
Additional recommendations and prevention tips:
- Spread the word. When suspicious activity is identified, immediately put an alert on the account or notify other departments, particularly customer service, to be on guard for unusual transaction requests.
- Ask more questions. Consider a policy to further verify the identity of the requester, either via the chat itself or through some other channel.
- Focus on purpose, not the communications method. Extend processes that are already in place for phone-requested wire transfers to chat-initiated wire transfers.
For example, if a contract is required to send wires over the phone, then the same should be in place for chat. If a PIN is required for phone wires, a PIN should be required for chat. (If neither contracts nor PINS are required currently, consider adding such policies.)
- Don't push that button so fast. Evaluate all account activity including account activity for suspicious behavior prior to releasing wire transfers, regardless of the channel through which the wire was submitted.
Don't let your guard down
Criminals are crafty. And they are taking advantage of every tool at their disposal to gain access to accounts, gather information, and move money.
Social engineering, stolen credentials, vishing, email account takeovers, and forgotten password features all make gaining access to online banking accounts a reasonably simple endeavor for a criminal and with no indicators on the victim's computer for an end-point detection solution.
Criminals use online banking as a vehicle to gather information about the account holder and their accounts--from basic account information to transactions to signatures--and then attempt transfers using the vehicle they think will be the most successful--online, offline via fax, check fraud, call center fraud, and now online customer service fraud.
There is no one single risk facing financial institutions today, but rather and ever-growing, ever-evolving matrix of schemes, with new twists on old schemes and inventive combinations.
Financial institutions are most well served by turning traditional fraud prevention techniques upside down. Rather than identifying specific threats or patterns, best practice and regulatory guidance recommends instead looking for unusual activity relative to typical behavior.
Given the dizzying matrix of human and technology-driven attacks, it is the only way to be prepared for the next new twist and innovative combination.
By Chris Silveira, manager, fraud intelligence, Guardian Analytics.
About Guardian Analytics
Guardian Analytics is a leader in online banking security solutions that detect and prevent internet banking fraud.
Tagged under Payments,













