Don’t get visually hacked
Visual privacy vulnerabilities provide entry points to sensitive data in financial services
- |
- Written by Dan Burks, U.S. Bank

Information security attacks are increasing both in their frequency and their cost to businesses, according to many current studies.
In response, information-security spending is reaching new heights. According to Gartner, global organizations are expected to spend just shy of $77 billion on information security in 2015, up more than 8% from 2014.
As organizations seek to give both employees and customers greater access to sensitive information through mobile devices, kiosks, and other technologies, they must take care to visually secure and help protect that information from what is known as “visual hacking.”
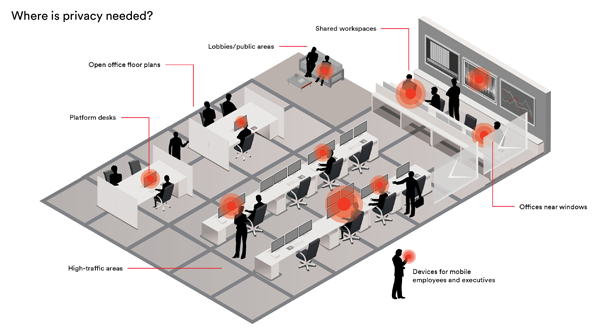
The eyes have it
Visual hacking is the viewing or capturing of sensitive, confidential, or private information for unauthorized use. Also known as “shoulder surfing” or “visual eavesdropping,” visual hacking is generally considered a low-tech threat that exploits the lapses in organizations’ visual privacy security.
This low-tech spying can be as simple as a visual hacker seeing an employee’s network log-in information taped to a computer monitor. By simply memorizing that information, the hacker now has access to the organization’s network and everything on it—financial records, intellectual property, sensitive customer details and more.
In the financial services world, security equals trust. When a customer walks into a bank, they will take notice of and appreciate the additional efforts you take to protect their information.
Consumers rarely suffer financially following a data breach, but they are forced to deal with the hassle of canceling accounts, monitoring alerts, ordering credit reports, and more. What’s worse, hackers who obtain embarrassing or compromising information about a person may use it to extort money from them.
Financial institutions lose too. The 2015 Cost Of A Data Breach study conducted by Ponemon Institute and IBM identified that financial institutions stand to lose 5.6% of customers following a data breach.
Steps to take
A strong visual security system can be realized using three key elements: assessment, policy and technology.
1. Assessment
Security threats can’t be effectively managed unless they’re properly understood. Identify opportunities where unauthorized individuals can view sensitive information.
2. Policy
Security policies and procedures should incorporate visual privacy protections. Place visual privacy warning labels on equipment such as printers, copiers, and fax machines.
Office, workstation, and technology layouts should be designed with visual privacy in mind.
Computers should be password protected and shut down when not in use. Once policies and procedures are in place, reinforce them through training, communications, and unscheduled audits.
3. Technology
A host of technologies are available to support visual privacy security both inside and outside an organization’s walls.
Physical privacy filters are available for computer monitors, laptop screens, and mobile devices. These filters are fitted directly over the screen and blacken out the views of anyone attempting to view the screen from an angle.
User-access technology on printers, copiers, and fax machines require employees to enter a passcode before they can retrieve, copy, or send files.
Document shredders should be placed near printers, copiers and fax machines, as well as by employees who frequently handle documents with sensitive information.
About the author
Dan Burks is U.S. Bank’s chief privacy officer, and wrote this article on behalf of the Visual Privacy Advisory Council. Members of the Visual Privacy Advisory Council receive compensation from 3M in connection with their participation.
Tagged under Risk Management, Cyberfraud/ID Theft, Feature, Feature3,