Beware business email compromise scam
“Innocent” communications, good intentions, and crooks combine to defraud via wire requests
- |
- Written by Steve Cocheo
 Could your business customers detect a fraudulent email, purportedly from their CEO, or would their financial staffers likely execute a fake wire transfer order?
Could your business customers detect a fraudulent email, purportedly from their CEO, or would their financial staffers likely execute a fake wire transfer order?
“I’rn a fake.”
Did you just read that sentence as “I’m a fake”?
Did you really? That’s not what it says.
Go back and read it again. There’s a good chance you didn’t catch that there is no “m” in that sentence, only an “r” and an “n” that your eye or your hurry made you read as an “m.”
This is not a new puzzle page for Banking Exchange, but a small part of a warning about email fraud that may be hitting your business customers, and, in the process, your bank.
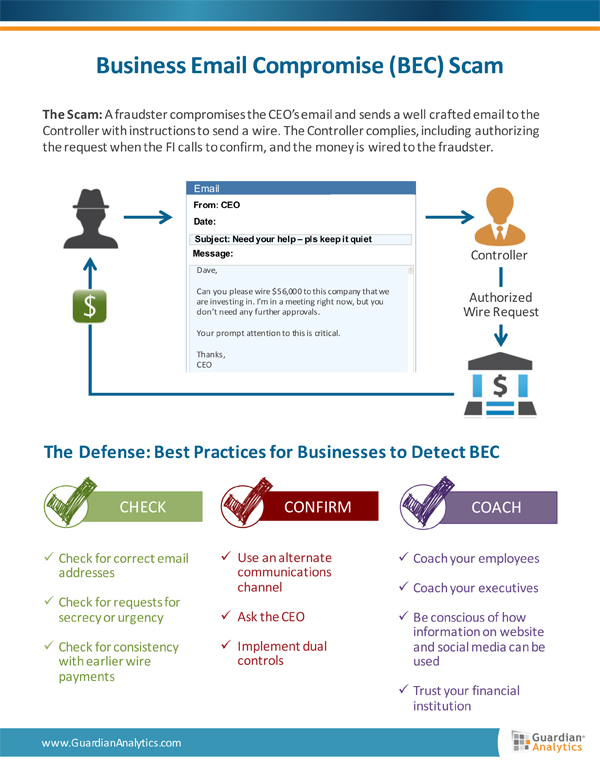
Criminals have been getting clever with phony email domain names that look like legitimate ones, such as that little trick above. Receiving an email from [email protected] could look like [email protected]. But that is just one way that a bank and its customers can be hit in a business email compromise scam, according to Chris Silveira, fraud intelligence manager at Guardian Analytics. The company says the most current estimate is that over 12,000 companies have been defrauded of over $2 billion using this scam.
Watch out for emails ordering big wires
Business email compromise scams began to surface in the middle of 2014 and picked up over 2015 into this year, according to Silveira.
The basic fraud runs as follows. A criminal compromises or fakes the email account of the CEO of a business. This access is used to send carefully crafted instructions to send a wire transfer. Typically the email is sent to the firm’s comptroller or other financial staff who have the ability to send a wire transmission. Usually the bank the wire is drawn on will call to confirm that the order is legitimate, and, unfortunately, to the comptroller’s knowledge that is so. The funds are wired to the fraudster, who wastes no time taking the money.
“At a fundamental level,” says Silveira, “BEC scams are well-researched phishing scams.”
How they can happen relies on a number of causes, ranging from infiltration of company systems to social engineering used to orchestrate aspects of the fraud, according to Silveira.
Silveira says that many business email systems have been hacked, enabling criminals to hijack an email account of a CEO in order to issue wire transfer orders. This access not only allows them to use the account—typically when the executive is out of the office—but to get a sense of how the CEO uses language in messages.
Imitation may be a form of flattery, but it also makes a dandy crowbar against people’s caution. Crooks are scouting for idiosyncratic words and phrases that their target uses, all the more to appear legitimate.
“People have to slow down, and look at what they’ve received in the emails, and what they are being asked to do,” Silveira says.
Hijacking the email from the system is not the only way in. An easier path has been found by some criminals because of the increasing mobility of company email.
With many firms allowing employees to use their own mobile devices to access email using web access email, hijacking an executive’s account has become easier. Frequently logging onto such systems takes only a short password.
“Criminals don’t have to hack into company systems when there’s web-enabled access,” says Silveira.
What they can learn about you
In the folk tale Hansel and Gretel, the children find their way home again because they thought to leave a trail of breadcrumbs on their trek to the witch’s house. After they do her in, they follow the trail in reverse.
Conversely, today we leave a great deal about ourselves on the internet, intentionally and unintentionally, so the bad guys can follow the bread crumbs to where we live.
Criminals have a wonderful incentive system for spending lots of time researching a target on the web: greedful gain. They can pick up details about an executive from overly descriptive social media references, even, for example, clues to when CEOs will be on the road. Silveira recommends taking greater care what is visible on the public views on social media sites, restricting any detail that could help a crook to the controlled network of contacts maintained for that account.
Overall, he says, mention nothing on the internet at all that you wouldn’t feel comfortable with the public at large knowing.
“Keeping it simple is the best way to go,” says Silveira. That, and keeping a distance between work-related social media use and that done for personal use.
Likewise, Silveira warns that free email systems can be very leaky, and that usage of these services for business—for taking work home or because a work system has gone down—can expose executives’ communications to fraudsters. This goes beyond email itself, to include calendar programs on those free services that may indicate when an executive is going to be out of town.
Guardian has put together detailed tip sheets of use to both banks and the customers whose wire transfer orders might be compromised. From the bank perspective, the five key areas to review are analysis of behavior; investigation of requests; authentication of payments; communication with customers when suspect transactions arise; and reporting fraudulent wires to the authorities, including filing a suspicious activity report (SAR).
Download Guardian Analytics Kit for businesses
Download kit for financial institutions