Watch out for mobile money risks
New Exam Council guidance gives reason for caution
- |
- Written by John Ginovsky
 Mobile banking can pose numerous risks to banks offering it to customers, according to new, ulcer-inducing advisory from federal banking regulators.
Mobile banking can pose numerous risks to banks offering it to customers, according to new, ulcer-inducing advisory from federal banking regulators.
While not necessarily intending to dump cold water on the plans of any bank to institute mobile financial services—or on those already offering them—the recently published Appendix E to the FFIEC Information Technology Examination Handbook certainly should give bank leaders pause.
The new section focuses on the risks associated with mobile financial services and emphasizes an enterprise-wide risk management approach to effectively managing and mitigating those risks.
And what risks—and what mitigation approaches—it outlines!
Document spells out mobile’s downsides
It behooves any bank’s CEO, CIO, CFO, CISO, legal counsel, and any and all other members of the leadership team to study this in detail.
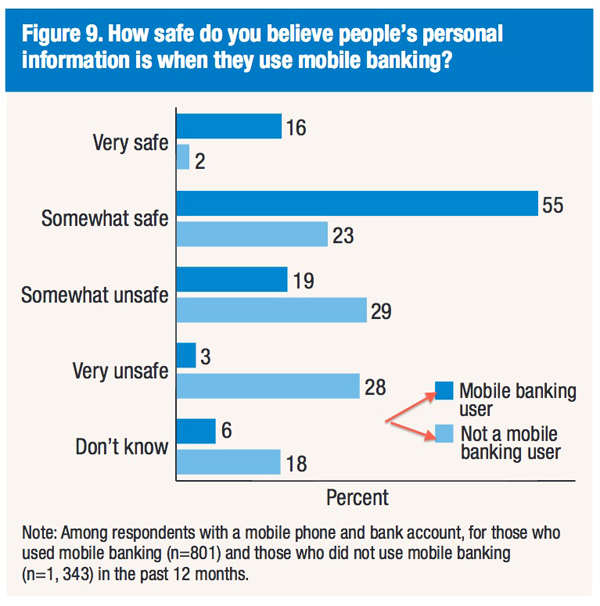
After all, the Federal Reserve in a March survey report says that concern about the security of the technology is a common reason consumers give for not using mobile banking or mobile payments (73% and 67% respectively). [See BE coverage, “Mobile banking upwardly mobile.” The chart below comes from the Fed survey report.]
FFIEC’s new appendix serves to, first, identify the risks (at least most of them, which are many), and, second, provide ways to deal with them. Bank leadership, once it takes sufficient measures, then can work to assure potential customers about mobile banking security.
To start, FFIEC acknowledges that “the mobile channel provides an opportunity for financial institutions of all sizes to increase customer access to financial services and decrease costs.”
But there’s a catch. It continues: “Although the risks from traditional delivery channels for financial services continue to apply to mobile financial services, the risk management strategies may differ.”
Regulators’ views on mobile risks
The following summarizes the risks and mitigation approaches detailed in the FFIEC appendix.
At the outset of the appendix, FFIEC states:
“Management should incorporate the identification of risks associated with mobile devices, products, services, and technologies into the financial institution’s existing risk management process … The identification process should include risks at the institution and those associated with the use of mobile devices where the customer implements and manages the security settings.”
Specific risks identified by the Exam Council:
• Customer in the driver’s seat. An institution may transfer to the customer the ability to implement security settings, increasing dependence on the customer to manage controls over sensitive financial data. Then there’s simple physical risk: The portability of mobile devices can lead to them being misplaced or stolen.
The mobile channel, with its emphasis on personalization and transmission of data, risks disclosure of personal information.
• Target of opportunity. The prevalence of mobile devices, common operating systems, and downloadable applications make these devices a target for malware and viruses. Personal identification numbers may not be adequate to protect data stored on a mobile device.
• Self-service infiltration. Criminals can compromise mobile application-based financial services with rogue, corrupted, or malicious applications that a customer downloads to his or her device.
• Texting toward the edge. Short message service (SMS) messages typically are not encrypted and are vulnerable to spoofing.
• “Al’s Bargain App Store.” On some mobile devices it is possible for users to download applications from sources not authorized by the device manufacturer, and which haven’t been evaluated for security protections.
• Flawed building blocks. Mobile web browsers are common starting points for malicious attacks.
• Insufficient armor. The lack of anti-phishing and anti-cross-site scripting capabilities increases the possibility of data loss on mobile devices.
• Messing with the heart of devices. Some devices allow the end user to access “root” information that can alter privileges in the operating system of the device. Also, in a process called “jail-breaking,” users can remove the manufacturer’s device controls or core operation system controls. These behaviors can allow a malicious user to transfer applications from untrusted sources.
• “What’s encryption?” Many applications store usernames, passwords, and email address in clear text.
• “Who’s in charge?” The mobile ecosystem is extremely decentralized, allowing for vulnerabilities to remain unremediated.
• “Exposure as a Service.” Because mobile financial services functions are not native on the customer’s device, vulnerabilities may be introduced. And communications of payments at the point of sale via NFC can be intercepted by malicious third parties. Malicious actors, using stolen identity information, may establish fake accounts on NFC-enabled mobile devices.
• Newcomers who faux pas. Entities outside the financial services industry may provide new applications without taking into account the industry’s regulations and supervisory expectations.
Fighting mobile risks
That’s a formidable list. In response, the regulators recommend a multi-layered approach to mitigating operational risks. On this the agencies said:
“This may include implementing security techniques at the service and database level; using transaction monitoring and geolocation techniques to identify anomalous … transactions; implementing and refining fraud prevention, detection, and response programs that facilitate rapid notification of potentially fraudulent transactions; applying additional controls (e.g. stronger authentication, encryption) to prevent unauthorized access to sensitive customer information stored on the device; and educating customers and employees to identify social engineering attempts that could lead to fraud.”
Now, the risk mitigation approaches recommended by the Exam Council:
• Educate your users. Make reasonable efforts to inform customers about the need to maintain the physical and logical security of mobile devices and suggest that users regularly install operating system and firmware updates.
• Nail it from the get-go. Have policies and procedures to verify a customer’s identity when enrolling for mobile payment systems. Have a process to authenticate users, including the possible use of biometric or out-of-band technology.
• Use it and dump it. Applications should not retain sensitive customer information on the device. And the application should wipe any customer information from memory when the customer exits the application.
• Assess risks before launching. Use threat-modeling when developing new mobile applications.
• Security within security. Require separate log-on credentials for mobile apps, in addition to those used to access the device. And require re-authentication whenever the device or application is unused for a designated period of time and each time the user launches the application.
• Pay attention to what’s going on. Maintain logging and monitoring capabilities on all applications to track customer activity and security changes, and to identify anomalous behavior and transactions.
More risk-fighting techniques
The appendix continues with extensive bullet-point lists dealing specifically with risks associated with SMS technology, mobile-enabled websites, mobile applications (even more than those listed above), mobile payments, compliance, and reputation harm. Further sections deal with monitoring and reporting.
After expanding on all the risks and mitigation approaches, the new appendix includes a step-by-step work program examiners may use to evaluate a given bank’s preparation—at the same time giving the bank’s leadership a framework for its own internal evaluation.
Words to live by, as FFIEC says in the appendix’s introduction: “Management should identify, measure, mitigate, and monitor the risks involved and be familiar with technologies that enable mobile financial services.”
Tagged under Payments, Risk Management, Mobile, Cyberfraud/ID Theft, Feature, Feature3,