Wannacry might be precursor of “Big One”
Cybersecurity preparedness must be ratcheted up further
- |
- Written by John Ginovsky
- |
- Comments: DISQUS_COMMENTS
 Bank tech trends can make your head spin. So regularly longtime Tech Exchange Editor John Ginovsky does his best to “make sense of it all.”
Bank tech trends can make your head spin. So regularly longtime Tech Exchange Editor John Ginovsky does his best to “make sense of it all.”
The recent global ransomware attack dubbed “Wannacry” likely, and hopefully, will serve as a wake-up call for everybody on the internet to pay attention to their cyber defenses.
Reports indicate that more than 230,000 users in 150 countries had their computer screens taken over by an ugly red page on which the criminals demanded $300 in bitcoins, or else all data would be wiped.
Fortunately, it seems that no U.S. banks were so targeted, according to the Financial Services Information Sharing and Analysis Center.
“What we know at this stage is that the majority of the attacks appear to be targeting and impacting nonfinancial sector entities around the world,” FS-ISAC said in a statement issued soon after the attack.
FS-ISAS added: “Financial institutions participating in information sharing with properly patched systems and better cyberhygiene are positioned to stay ahead of cybercrime.”
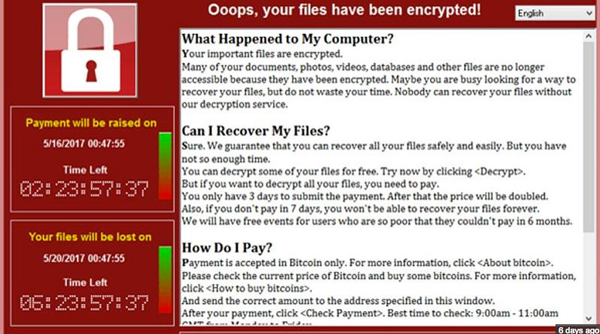
Fortunately, most WannaCry cyber attacks—which include the screen above—don’t appear to have hit banks.
No doubt. ABA, for example, urges all banks to join the 7,000 or so institutions that currently participate in FS-ISAC, for their own, and everybody’s protection.
There but for …
But it’s sobering to consider what a close call this really was for U.S. banks. As recounted in a podcast sponsored by Wharton School of the University of Pennsylvania, a big reason the United States in general was spared was because one researcher found a “kill switch” that effectively contained the attack—at a cost of about $11.
“This was not the big one,” said Andrea Matwyshyn, professor of law and computer science at Northeastern University, during the podcast. “This was a precursor of a far worse attack that will inevitably strike—and it is likely, unfortunately, that [the next] attack will not have a kill switch.”
The cyber hijackers used a data vulnerability tool—purloined from the National Security Agency—to attack outdated Microsoft systems, mainly Windows XP.
The vulnerability should not have been a shock. It was widely reported in 2014 that Microsoft would no longer issue patches for XP. Presumably, most banks and most businesses took that announcement seriously and upgraded to better-protected systems. Microsoft, for its part, following the latest attack issued updates for computers that use the Windows XP, Vista, Windows 7, and Windows 8 operating systems.
Microsoft, in fact, in March issued a security update to patch the specific vulnerability for its then-protected systems. The subsequent victims, then, were those who ignored or otherwise neglected to affix this patch.
Brad Smith, president and chief legal officer, wrote this in a blog soon after the attack occurred:
“This attack demonstrates the degree to which cybersecurity has become a shared responsibility between tech companies and customers … This attack is a powerful reminder that information technology basics like keeping computers current and patched are a high responsibility for everyone, and it’s something every top executive should support.”
Redoubling redoubled efforts
Again, U.S. banks seem to have dodged a bullet on this particular attack. Cybersecurity in the banking industry has long been top of mind in C-suites, as well as by bank regulators—probably to a higher degree than in most other business sectors. Still, the world has changed and that attention will only need to be ratcheted up.
For example, a Deloitte Global Survey in March came to this conclusion: “A majority of banks and other financial institutions surveyed are not confident about their firms’ effectiveness in managing cybersecurity and geopolitics, two of the biggest risks facing global businesses of all shapes and sizes.”
Deloitte came to this conclusion by factoring in a wide variety of influences. These included issues around deregulation; new automated tools intended to better serve customers; and renegotiations of international trade agreements.
But taken together, Edward Hida, Deloitte Global Risk and Capital Management Leader, says this:
“Risk management is becoming even more important today, as financial institutions confront a variety of trends that have introduced greater uncertainty into the future direction of the business and regulatory environment. Risk management programs will need to not only become more effective and efficient, but also acquire the agility to respond flexibly and nimbly to the next set of demands.”
Safer versus faster
The basic issue facing bank cyber defenses comes down to vulnerability—and plugging all the gaps as soon as they can be identified.
But it’s not that simple. At the same time, most banks are wrangling with new demands from their customers for increased, easier, and faster access and services. That opens huge gaps.
“Twenty-four percent of banks worldwide struggle with the identification of their customers when delivering digital and online banking services,” says Kaspersky Lab in a recent survey. Kaspersky goes on to say: “With the rise of online and mobile banking, customers are not only becoming victims of financial fraud, but also a major entry point for attacks on banks’ digital channels.”
It’s an old story. Banks need their customers to be happy—but only if they really are their customers. That means proper and strong forms of authentication are needed, but not if they are too hard to use.
“In addition to two-factor authentication and other security procedures used by banks, Kaspersky Lab recommends implementing dedicated solutions that can help to identify whether a person is authorized to access the account, without requiring additional actions from the user,” it says.
Lots of people and companies have focused on this. Two avenues that seem to have traction are advanced biometrics and security analytics.
Eyeverify Inc., which specializes in eyeball-based forms of authentication, issued a report which, unsurprisedly, shows many customers have confidence in biometric-based authentication. Still, when 86% of any survey group agree that biometrics makes logging into apps easier than typing in a password, it’s worth taking note of. And the point the company makes about how people who currently use fingerprint scanning—such as on iPhones, etc.—are more likely to use other forms of biometrics, makes some sense.
Meanwhile SAS, the huge analytics and data company, teamed with Ponemon Institute and came up with a survey of IT professionals. They concluded that smart systems that analyze data proactively can improve security operations. The big caveat is, that data needs to be configured correctly and tuned to the particular system, in order for it to be really effective. That all remains to be worked out, it seems.
6 steps to take post-Wannacry
So back to the immediate threat of ransomware. After the Wannacry attack, EY quickly issued a list of half a dozen steps organizations should take right away:
• Disconnect infected machines from the network and take all backups offline.
• Activate the incident response plan and don’t treat the investigation as merely an IT issue or exercise.
• Identify and address vulnerabilities in the organization’s connected ecosystem; install security updates, malware detection, and anti-virus detection.
• Ensure systems are patched before powering up PCs, and maintain a robust, enterprise-level patch and vulnerability management program.
• Activate business continuity plans.
• Collect and preserve evidence in a forensically sound manner so it is conducive to investigation.
Long term, though, Microsoft’s Brad Smith has some good advice: “We should take from this recent attack a renewed determination for more urgent collective action. We need the tech sector, customers, and governments to work together to protect against cybersecurity attacks. More action is needed, and it’s needed now.”
Sources used for this article include:
FS-ISAC Response To WannaCry Ransomware Attack
How The Wannacry Attack Will Impact Cyber Security
Security Analytics Proves Challenging But Effective, Finds Survey By SAS And Ponemon
Need For Urgent Collective Action To Keep People Safe Online: Lessons From Last Week’s Cyberattack
Tagged under Management, Lines of Business, Risk Management, Blogs, Making Sense of it All, Cyberfraud/ID Theft, Feature, Feature3,














